TECHNOLOGY
Palo Alto Networks: Poor software supply chain impacts cloud infrastructure
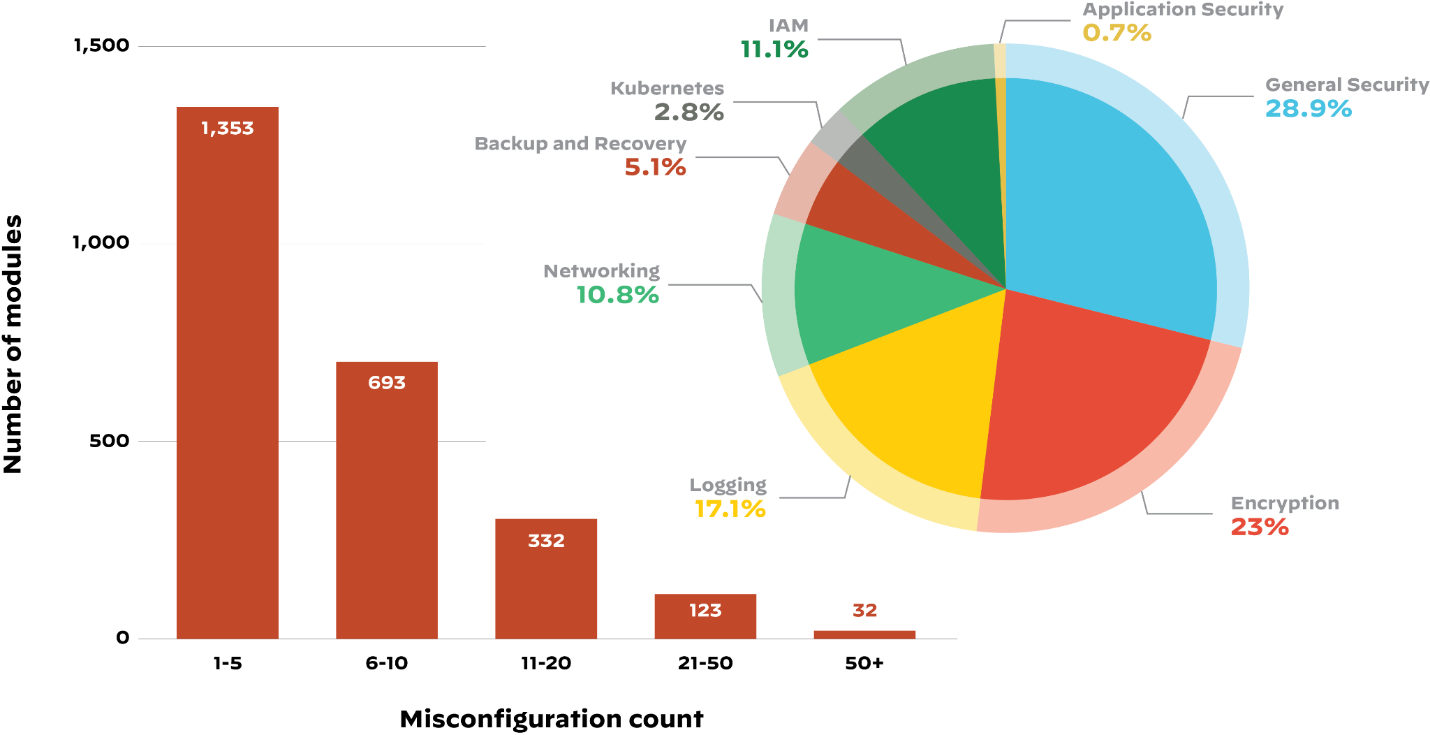
As an example of the prevalence of misconfigurations, Unit 42 researchers analyzed public Terraform modules by number of misconfigurations (left) and types of misconfigurations and their percentages (right). Source: Unit 42 Cloud Threat Report, 2H 2021.
Posted on Nov. 19, 8:48 p.m.
HIGH-PROFILE software supply chain attacks such as SolarWinds and Kaseya have shed a glaring light on the disparity between organizations’ perceptions of security within their cloud infrastructure, and the reality of threats in their supply chains that can impact business catastrophically.
In the latest Palo Alto Networks’ Unit 42 Cloud Threat Report, 2H 2021, Unit 42 researchers dive deep into the full scope of supply chain attacks in the cloud and explain often misunderstood details about how they occur.
They also provide actionable recommendations any organization can adopt immediately to begin protecting their software supply chains in the cloud.
The Unit 42 team analyzed data from a variety of public data sources around the world in order to draw conclusions about the growing threats organizations face today in their software supply chains.
Their findings indicate that many organizations may have a false sense of security in the cloud and in reality are vastly unprepared for the threats they face.
In addition to analyzing data, Unit 42 researchers were commissioned by a large SaaS provider (a customer of Palo Alto Networks) to run a red team exercise against their software development environment. In just three days, a single Unit 42 researcher discovered critical software development flaws that left the customer vulnerable to an attack similar to that of SolarWinds and Kaseya.
Key Findings
Poor Supply Chain Hygiene Impacts Cloud Infrastructure
The large SaaS provider detailed in the red team exercise has what many would consider a mature cloud security posture. However, during the exercise, Unit 42 researchers were able to leverage misconfigurations in the organization’s software development environment, such as the presence of hardcoded IAM key pairs, that would have allowed them to control all development processes and thus conduct a successful supply chain attack.Further, Unit 42 researchers found that 21% of the security scans they ran against the customer’s development environment resulted in misconfigurations or vulnerabilities, highlighting how process gaps and critical security flaws leave an organization exposed and susceptible to a business-halting attack.
Third-Party Code Is Rarely Trustworthy
In their research, Unit 42 researchers discovered that 63% of third-party code templates used in building cloud infrastructure contained insecure configurations, and 96% of third-party container applications deployed in cloud infrastructure contain known vulnerabilities. With this level of risk, an attacker could easily gain access to sensitive data in the cloud and even take control of an organization’s software development environment. Based on the Unit 42 team’s findings, it’s evident that unvetted code can quickly snowball into a security breach, especially as infrastructure flaws can directly impact thousands of cloud workloads. For that reason, it is critical that organizations understand where their code is coming from since third-party code can come from anyone, including an Advanced Persistent Threat (APT).
Conclusion: Organizations Need to Shift Security Left
Teams continue to neglect DevOps security, due in part to lack of attention to supply chain threats. Cloud native applications have a long chain of dependencies, and those links have relationships of their own. DevOps and Security teams need to gain visibility into the bill of materials in every cloud workload in order to evaluate risk at every stage of the dependency chain and establish guardrails.
TECHNOLOGY
TECHSHAKE announces strategic business alliance with Mirai Works

6:00 p.m. July 18, 2024
TECHSHAKE PTE. LTD., headquartered in Makati City, Philippines, with a branch office in Singapore, is pleased to announce that it has entered into a business alliance agreement with Mirai Works Inc., headquartered in Minato-ku, Tokyo, a professional-focused human resource service provider in Japan.
This alliance aims to provide support for the growth and market entry of startups in Japan and Southeast Asia.
TECHSHAKE’s Business
TECHSHAKE’s vision is to expand the startup ecosystem in Southeast Asia, with a focus on the Philippines, and to connect Southeast Asia with the world.
TECHSHAKE (Kotaro Adachi, CEO & Co-Founder) manages and runs the Philippines’ premier innovation conference “IGNITE” in collaboration with dentsu X, a subsidiary of Dentsu Inc. and a provider of integrated media planning, branding, and marketing services. Furthermore, TECHSHAKE operates media platforms, matches startups with established companies and investors, and provides essential support for startups to thrive.
TECHSHAKE is committed to fostering a global environment for business development in the Philippines.
TECHSHAKE is dedicated to nurturing the startup ecosystem in Southeast Asia by connecting entrepreneurs with the necessary resources and networks to succeed. With a strong presence in the Philippines and extensive experience in supporting startups, TECHSHAKE aims to bridge the gap between Southeast Asia and global markets.
Mirai Works (Nagaharu Okamoto, CEO & Co-Founder) is driven by a mission to empower individuals to embrace challenges that shape the future of Japan. Their vision is to cultivate an ecosystem where professionals thrive, regardless of traditional work structures. They are developing a business to provide opportunities for professionals to navigate changes throughout their careers and to support them in the midst of diverse career paths, including independence, entrepreneurship, side businesses, and full-time employment.
Mirai Works’ initiatives aim to provide resources for individuals to succeed in an evolving work landscape, fostering innovation and growth.
In May 2023, Mirai Works launched “Booster,” (https://booster.mirai-works.co.jp/) a startup support platform aimed at empowering professionals to start and scale their businesses. Booster facilitates growth through acceleration programs, providing information regarding startup ecosystem events and pitch competitions, and personalized mentorship, ensuring startups have access to critical resources for success.
In this collaboration, TECHSHAKE will leverage its expertise and network to support Japanese startups looking to enter the Southeast Asian market. Mirai Works, known for its professional human resource services and startup support platforms, will enhance TECHSHAKE’s efforts by providing hands-on support in various aspects of business promotion. This partnership underscores Mirai Works’ commitment to facilitating cross-border collaboration and growth opportunities for startups in Japan and Southeast Asia.
Details of Cooperation
Not only does Mirai Works support startups registered with Booster, but it also offers a service called “Free Consultant,” (https://freeconsultant.jp/) a freelancer business matching platform. Through Free Consultant, Mirai Works plans to connect highly skilled professionals with Southeast Asian startups supported by TECHSHAKE. Mirai Works provides hands-on support in various aspects of business promotion, including management strategy planning, marketing and PR, IPO preparation, and M&A activities, to drive business growth. Furthermore, Mirai Works will collaborate with TECHSHAKE to hold acceleration programs and offer support for overseas expansion.
TECHNOLOGY
Last Call for Entries to the OPPO imagine IF Photography Awards 2024

8:59 p.m. July 15, 2024
OPPO today issued a last call for entries to the OPPO imagine IF Photography Awards 2024. Since the competition was launched on January 17, over one million submissions have been received from 73 countries and regions, each showcasing a vibrant tapestry of cultures and traditions from around the world. As the global submission deadline approaches on July 28, OPPO is calling on photography enthusiasts to seize the final opportunity to capture spectacular moments through the lens of their cameras and collectively demonstrate the power of mobile imaging.
imagine IF Campaigns Gather Inspiring Work from around the World
Since inaugurating the competition at the start of the year, OPPO has initiated a series of themed activities aimed at encouraging its global user base to use the power of images to expand their imaginative boundaries. From May to July, coinciding with Mother’s Day and the beginning of the summer season, the ‘Road to Paris’ campaign invited users to portray the grace of mothers and capture the excitement of sport through the photographic lens for the chance to win a spot at Paris Photo 2024. The ‘In Sync with the World’ campaign meanwhile sought images that portrayed exploration around the world. Across both campaigns, the wide breadth of entries received showcased strong and emotive works that help to foster exchange and understanding between different cultures.

Photo 1 Shot by Isthisreal; Photo 2 Shot by Andrewoptics; Photo 3 Shot by Shisan and Petrichor
Celebrating Culture in All Its Diversity
Many of the entries submitted so far this year have seen participants from around the world showcase the unique landscapes and traditions of their home countries through stunning photographs. From the lively coastal life of Rio de Janeiro to the profound natural wonders of the Amazon rainforest, each image offers a portal into a new world for audiences to step into.
Alongside the main OPPO imagine IF Photography Awards, OPPO has also collaborated with Discovery Channel to showcase the diversity and allure of world cultures through the ‘Culture in a Shot’ program. Kicking-off in June in northern Thailand, the program has so far seen OPPO capture traditional crafts and musical instruments in a series of captivating images that bring the region’s rich and colorful cultural heritage to global audiences while advocating for deeper cross-cultural exchange.

Shot by Jerome Teo
Share Your Imagination for the Chance to Win Incredible Prizes
Entries for the OPPO imagine IF Photography Awards 2024 remain open until 24:00 (UTC+8) on July 28. Submission to this year’s competition will be judged by a prestigious global judging panel that includes the likes of contemporary photography icon Steve McCurry, together with National Geographic Photographer Michael Yamashita, Hasselblad Master Tina Signesdottir Hult, Magnum Photos member Alec Soth, and OPPO Senior Vice President and Chief Product Officer Pete Lau. A series of exciting awards are on offer to all participants, including individual prizes of up to USD24,000 and the chance to have their work exhibited at Paris Photo 2024.

Schedule and Prizes of OPPO imagine IF Photography Awards 2024
More than just a photography competition, the OPPO imagine IF Photography Awards is a platform for cultural exchange and creative inspiration. All photography enthusiasts are invited to take part and share moving moments that ignite inspiration and imagination through the global platform. To learn more about the OPPO imagine IF Photography Awards and to submit an entry, please visit the official website at https://imagine-if.oppo.com/en/.
TECHNOLOGY
ZTE CEO Xu Ziyang at MWC Shanghai 2024: Ingenuity for Solid Foundation, Openness for Win-Win

10:20 p.m. July 12, 2024
ZTE Corporation (0763.HK / 000063.SZ), a global leading provider of integrated information and communication technology solutions, announced today that the company’s CEO, Xu Ziyang, has delivered keynote speeches at both the “AI First” session and the GTI Summit themed “5G-A×AI” at MWC Shanghai 2024. Mr. Xu shared ZTE’s practices and innovations in intelligent digitalization amidst the AI wave.
In his keynote speech at the “AI First” session, Xu Ziyang shared insights under the theme “Ingenuity for Solid Foundation, Openness for Win-Win.” He emphasized that while the world has already entered an AI-driven industrial revolution, the development of generative AI faces challenges that extend from hallucinations, security, and ethics, to computing power, energy consumption, datasets, standardization, and commercial applications. To address these challenges, ZTE proposes three major principles: openness and decoupling, computing and network evolution, and training and inference enhancement.
Centered on customer value, ZTE provides a full-stack and full-scenario intelligent computing solution encompassing computing power, networks, capabilities, intelligence, and applications. This establishes a robust foundation through technical expertise and fosters innovation through collaborative partnerships, aimed at empowering various industries in their digital transformation. By continuously injecting momentum into high-quality economic development, ZTE plays a pivotal role in shaping a brighter future in the AI era.
At the GTI Summit during MWC Shanghai 2024, Xu Ziyang participated in the GTI-GSMA 5G-A×AI cooperation signing ceremony and delivered a speech titled “Computing and Network Evolution Towards an Intelligent Future.” He detailed the transition from traditional industrialization to new industrialization, addressing core challenges, proposing solutions, and citing practical cases. The critical pathway involves breakthroughs in core digital and intelligent technologies, enhancing infrastructure efficiency and capability, and deeply integrating industry expertise. This accelerates the convergence of digital and physical realms, enhances production and transaction efficiency, and establishes agile, resilient organizations prepared for an uncertain future.
According to Mr. Xu, ZTE advocates focusing on four dimensions – digitalization, networking, intelligence, and low-carbon initiatives – to tackle current challenges and drive continuous innovation and development. The company promotes openness and decoupling, unleashing superior computing with advanced networks, enhancing intelligence capabilities, and driving business growth through green initiatives, with a strong commitment to vigorously supporting the healthy and sustainable development of the industry chain, fostering a thriving digital economy.
Below is the original text of Xu Ziyang’s speech titled “Ingenuity for Solid Foundation, Openness for Win-Win”:
Good day, everyone. It’s an honor to be invited to speak here at the MWC Shanghai. Today, I’d like to share ZTE’s insights and practices under the theme of “Ingenuity for Solid Foundation, Openness for Win-Win”.
Embracing Changes and Promoting Intelligent Evolution
Over the past year, large language models and generative AI have accelerated the transformation towards an increasingly digital and intelligent world. With the rapid emergence of new technologies and products, new business scenarios and models are also gaining momentum. Although generative AI is still in the early stage, there is a growing consensus that the world has already entered an AI-driven industrial revolution. AI will have disruptive and far-reaching impacts on all aspects of production and life, and significantly reshape the global economic landscape. According to forecasts by a consulting firm, by 2030, AI will boost China’s GDP by 26% and North America’s by 14.5%. This is equivalent to USD 10.7 trillion and accounts for almost 70% of the global economic impact. Apparently, AI will bring unprecedented business opportunities in various sectors such as retail, financial services, and healthcare.
Apart from issues concerning hallucinations, security, and ethics, the development of generative AI also faces challenges in terms of computing power, energy consumption, dataset, standardization, commercial application, etc. Therefore, advancements in multiple areas are required. As such, ZTE proposes three major principles: computing and network evolution, training and inference enhancement, openness and decoupling.
First, to break through technology bottlenecks, it’s crucial to strengthen research on architectures, algorithms, computing networks, and hardware-software synergy, thus improving AI training and inference efficiency. Second, various solutions such as Retrieval-Augmented Generation (RAG) and AI agents should be employed to ensure reliability, security, and interpretability, thereby facilitating the widespread application of large models and higher value creation, and building a data flywheel that improves both capabilities and business efficiency. Finally, accelerating standardization through openness and decoupling will help build a thriving industrial and commercial ecosystem.
Building a Highly-Efficient Foundation Through Computing and Network Evolution
To begin with, we emphasize computing and network evolution to build a highly-efficient foundation. For intelligent computing, high-speed network connections are not just vital but also indispensable. From die-to-die connectivity to interconnects of chips, servers, and data centers, continuous innovation and breakthroughs in network technology will greatly enhance the performance and efficiency of intelligent computing.
More specifically, Die-to-Die (D2D) emphasizes high-speed interconnects between bare dies in a single package. Combined with the full series of in-house parallel and serial D2D interface IPs, as well as the advanced 2.5D and 3D packaging technologies, our solution enables heterogeneous integration and disaggregation. To a certain extent, challenges arising from the slowdown of Moore’s Law and constraints in manufacturing can be effectively mitigated. We have developed chip architectures that enable heterogeneous computing and network processing, which in turn deliver enhanced performance and cost efficiency.

















